Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
VMware Patches vCenter and NSX Vulnerabilities CVE-2025-41250, CVE-2025-41251, and CVE-2025-41252 - On 29 September 2025, Broadcom patched three high-severity vulnerabilities affecting VMware vCenter Server, VMware NSX, and related products, including NSX-T, VMware Cloud Foundation, VMware Telco Cloud Platform, and VMware Telco Cloud Infrastructure. There are no reports of these vulnerabilities being exploited. CVE-2025-41250 is an SMTP header injection flaw in vCenter, caused by improper handling of notification email headers in scheduled tasks. A user with task-scheduling permissions could exploit it to manipulate emails.
The other two affect NSX. CVE-2025-41251 concerns the password recovery mechanism, where inadequate validation could let an unauthenticated actor identify valid usernames. CVE-2025-41252 is a username enumeration vulnerability from improper input validation during authentication attempts, which could also allow discovery of valid usernames during login requests.
Cisco Patches Actively Exploited Stack-Based Buffer Overflow Vulnerability (CVE-2025-20352) Affecting IOS and IOS XE Software - On 24 September 2025, Cisco disclosed and patched CVE-2025-20352, a stack-based buffer overflow in the SNMP subsystem of Cisco IOS and IOS XE. Active exploitation in the wild has been confirmed, allowing threat actors to cause denial of service (DoS) or execute arbitrary code as root under certain conditions. The vulnerability affects all SNMP versions (v1, v2c, v3) on IOS and IOS XE, and can be triggered by specially crafted SNMP packets over IPv4 or IPv6. Low-privileged exploitation can force device reloads, while high-privileged exploitation may allow remote code execution.
Exploitation requires SNMP read-only community strings for v1/v2c or valid credentials for v3. Threat actors send crafted packets to trigger service interruptions or full system compromise. Cisco PSIRT confirmed in-the-wild attacks following incidents involving stolen administrator credentials. Exploitation patterns align with tactics used by advanced persistent threat (APT) groups and state-sponsored campaigns targeting Cisco network infrastructure.
Security Researcher Discloses Vulnerability Tracked as CVE-2025-56383 Affecting Notepad++ - On 26 September 2025, security researcher zer0t0 disclosed CVE-2025-56383, a command injection vulnerability in Notepad++ version 8.8.3. The flaw arises because Notepad++ automatically loads certain plugin DLLs at startup, which can be exploited if a malicious DLL with the same name is present.
Successful exploitation could allow a threat actor to execute arbitrary code. Notepad++ has not yet released a patch for the vulnerability, and there are no reports of active exploitation in the wild at the time of writing.
Potential Threats
Malvertising Campaign Distributes Trojanized Microsoft Teams Installer to Deliver Oyster Backdoor - On 26 September 2025, cybersecurity firms Conscia and Blackpoint Cyber published aligned technical analyses of a malvertising campaign that used trojanised Microsoft Teams installers to deliver the Oyster backdoor. The actors employed SEO poisoning and rogue advertisements to redirect users searching for legitimate Microsoft Teams installers to malicious domains such as teams-install[.]icu and teams-install[.]top; one documented redirect chain went from bing[.]com to team[.]frywow[.]com and then to teams-install[.]icu.
At the time of the analyses those domains returned error messages. The fraudulent installers were signed with digital certificates issued to entities including KUTTANADAN CREATIONS INC., 4th State Oy and NRM NETWORK RISK MANAGEMENT INC.; those certificates remained valid for two days, enabling the threat actors to evade signature-based detection and reduce the window for certificate revocation.
According to Blackpoint Cyber, the trojanised installer (MSTeamsSetup.exe) drops a DLL called CaptureService.dll into the user’s AppData\Roaming folder and creates a scheduled task named “Capture Service” that invokes rundll32.exe to run the DLL every eleven minutes. CaptureService.dll then installs the Oyster backdoor, which the actors used to communicate with a set of command-and-control servers, including nickbush24[.]com, techwisenetwork[.]com, maddeehot[.]online, server-na-qc2[.]farsafe[.]net, and the IPs 45[.]66[.]248[.]112, 54[.]39[.]83[.]187 and 185[.]28[.]119[.]228.
Analysis of the npm Package “fezbox” Using QR Code Steganography to Steal Browser Credentials - On 22 September 2025, cybersecurity firm Socket published an analysis of a malicious npm package called fezbox. Posing as a JavaScript/TypeScript utility library for QR codes and helper functions, fezbox covertly executes browser-based malware that steals credentials from cookies using layered obfuscation and QR‑code steganography. Socket attributed the package to an npm user calling themselves “janedu” (email: janedu0216[@]gmail[.]com).
When imported, fezbox loads several internal modules and checks for a browser context before attempting execution. If running in production and after passing a probabilistic execution check, it delays for 120 seconds then fetches a remote QR‑code image, extracts a hidden, obfuscated JavaScript payload from the image, and executes it. The payload reads document.cookie to retrieve values for username and password (obfuscated in the code), and - if present - sends them to a remote command‑and‑control endpoint; otherwise it exits. At the time of Socket’s report the remote image URL remained active and the endpoint returned an error.
Fileless Execution Technique Using In-Memory PE Loader to Bypass EDR - On 23 September 2025, security researcher Robbie Corley published a technical blog describing a fileless method for loading and executing 64‑bit portable executables (PE) entirely in the memory of a trusted process. The technique allows an operator to download and run remote PE files without writing them to disk, bypassing file-based endpoint detection and response (EDR) controls and minimising forensic artifacts.
Corley shared a loader script, peinjection.cpp, which requires the operator to hard-code the URL of the PE file and a user-agent. The script retrieves the PE, stores its raw bytes in memory, parses the headers, allocates space within the current process, and maps the sections correctly. It then applies relocations if needed, resolves imports by loading required DLLs, sets memory protections, and transfers execution to the PE’s entry point. This allows the payload to run entirely in the trusted process’s memory space without touching disk.
General News
Cyberattack on British retailer Co-op shaved about $275 million from revenues - The Co-op retail chain suffered a £206 million ($274 million) hit to revenues following a cyberattack in April that disrupted store operations and led to the theft of customer data. The incident, one of several high-profile hacks affecting U.K. businesses that spring, also targeted Marks & Spencer and Harrods. Four individuals, including a teenage minor, were arrested in July in connection with the attacks, which are believed to involve the Scattered Spider group, a loose network of young cybercriminals.
According to Co-op’s earnings report, its food business was hardest hit, with stock availability reduced as systems were proactively taken offline. CEO Shirine Khoury-Haq said staff worked “day and night” to restore operations, but stores continued to experience disruptions, impacting sales, promotions, and market share. While the company avoided a ransomware lockdown by disconnecting its networks, all 6.5 million members had data stolen. The total profit loss attributable to the attack in the first half of the year was £80 million ($106.7 million).
Afghanistan plunged into nationwide internet blackout, disrupting air travel, medical care - Authorities in Afghanistan shut down internet and telecommunications services nationwide this week, leaving millions without access to digital communication, banking, and essential public services. The blackout, confirmed by monitoring groups NetBlocks, Kentik, and Proton VPN, began late Monday and continued into Tuesday, affecting mobile, fixed-line, and telephone networks. It follows a partial disruption earlier this month when the Taliban blocked fiber connections in several provinces, citing a need to curb “immoral acts.”
The shutdown has had widespread consequences. Kabul’s airport saw few arrivals or departures, banking and payment systems were disrupted, and online education - critical for Afghan girls barred from classrooms - was interrupted. Several ministries’ websites went offline, TV stations were knocked off air, and international news agencies could not contact their Kabul bureaus. The UN and humanitarian organisations have struggled to maintain operations, relying on radios and satellite links. Activists reported the blackout has isolated citizens, particularly women, and silenced voices across the country, while governments worldwide continue to use internet restrictions to suppress dissent.
UK Retailer Harrods Reports Second Data Breach in Six Months, Affecting 430,000 Customer Records - On 27 September 2025, UK luxury department store Harrods disclosed a second data breach in six months, reportedly involving a third-party service provider. The unknown threat actor is believed to have exfiltrated 430,000 customer records, including names, contact details, marketing preferences, and loyalty card affiliations. Harrods confirmed that customer account credentials and payment information were not compromised, and its internal systems remained secure. The company also stated that this incident was unrelated to an earlier breach attempt in May 2025.
Harrods began notifying affected customers on 26 September 2025. Shortly afterwards, the threat actor reportedly contacted the company, but Harrods declined to engage. At the time of writing, most details about the attack - including the responsible parties and the targeted third-party provider - remain unknown.
Threat Actor Weekly Graph
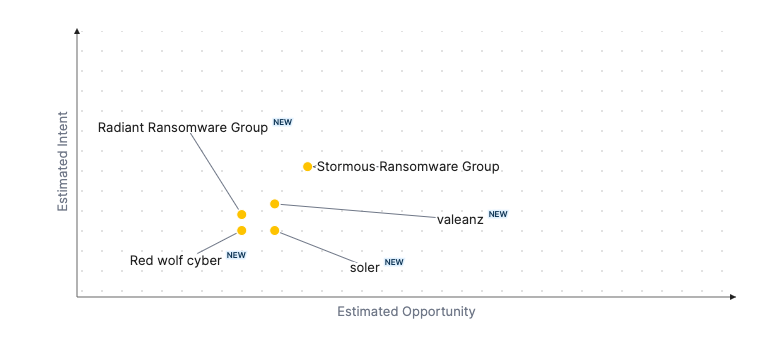
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group's severity. These updates can be seen below.
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Increase | Opportunity | Intent | ||||||
|---|---|---|---|---|---|---|---|---|---|
| valeanz | NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 35 |
| Radiant Ransomware Group | NEW | → | ● Basic | NEW | → | ● 25 | NEW | → | ● 31 |
| soler | NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 25 |
|
Red wolf cyber |
NEW | → | ● Basic | NEW | → | ● 25 | NEW | → | ● 25 |
| Stormous Ransomware Group | ● Basic | → | ● Basic | ● 49 | → | ● 35 | NEW | → | ● 49 |
Global Trends Powered by Recorded Future
Within each category, we have provided the current top five globally trending items. Each item is linked to how actively trending it is and is marked with a small symbol.
The spikes in references are calculated over 60 days and are normalised to ensure they aren't disproportionate when compared to bigger entities that will naturally have more baseline mentions.
▲- Spike – This indicates a large increase in reporting volume and a high diversity in the event descriptions,
▲- Rise – This indicates a small increase in reporting volume with little diversity in the descriptions.
| Attackers | Methods | Vulnerabilities | Targets | ||||
|---|---|---|---|---|---|---|---|
| Phantom Taurus | ▲ |
Inferno Drainer |
▲ | CVE-2025-32463 | ▲ |
Binance |
▲ |
|
Handala Hack Team |
▲ |
Phishing |
▲ | CVE-2025-41244 | ▲ |
Scotland |
▲ |
|
Cyber Partisans |
▲ |
Spear Phishing |
▲ | CVE-2024-3400 | ▲ |
Harrods |
▲ |
|
Lapsus$ Group |
▲ |
Backdoor |
▲ | CVE-2025-41251 | ▲ |
WestJet Airlines |
▲ |
|
Medusa Ransomware Group |
▲ |
Rowhammer |
▲ |
CVE-2025-59305 |
▲ |
Asahi Group Holdings, Ltd. |
▲ |
Prominent Information Security Events
Analysis of the npm Package “fezbox” Using QR Code Steganography to Steal Browser Credentials
Source: Insikt Group | Validated Intelligence Event
IOC: URL - hxxxs://my-nest-app-production.up[.]railway[.]app/users
IOC: URL - hxxxs://res[.]cloudinary[.]com/dhuenbqsq/image/upload/v1755767716
On September 22, 2025, cybersecurity firm Socket (@SocketSecurity on X) published an analysis of a malicious npm package named fezbox that posed as a JavaScript/TypeScript utility library (QR-code and helper modules). Socket attributed the package to an npm user using the alias “janedu”, registered with the email janedu0216[@]gmail[.]com. When imported, fezbox loads several internal modules — including decrypt-B6fiICsn.js, relative-5TnWB4bl.js, and qr/index.cjs — checks for a browser context using typeof window and typeof document, performs an execution-probability check (allowing one successful run in three attempts), and if in a production context delays further action for 120 seconds. It then instantiates a QRCodeScriptLoader, decodes a reversed string to reveal a Cloudinary link (hxxps://res[.]cloudinary[.]com/dhuenbqsq/image/upload/v1755767716/b52c81c176720f07f702218b1bdc7eff_h7f6pn[.]jpg), and fetches the referenced QR-code image; at the time of Socket’s write-up that Cloudinary URL remained active.
After fetching the image, the loader parses the QR code and extracts a hidden JavaScript payload embedded in the image via steganography. The payload is deliberately obfuscated (Unicode escape sequences and reversed strings) to frustrate static analysis and even includes a non-operational decoy line—"idbgha".split("").reverse().join()—to mislead automated scanners. When executed, the payload defines a function that reads document.cookie to extract values for username and password (the password value is disguised in the code as the reversed string "drowssap"). If both values are present the script issues an HTTPS POST to the actor-controlled endpoint hxxps://my-nest-app-production[.]up[.]railway[.]app/users; Socket reported that the endpoint returned an error message at the time of writing. If the cookie values are not found, the payload exits without further action.
Taken together, Socket’s analysis shows a layered, evasive credential-stealing operation: a supply-chain delivery via a trojanized npm package, delayed and probabilistic client-side execution, remote QR-based payload delivery, and multiple obfuscation techniques to avoid detection. Socket attributes this campaign to the npm alias janedu, and the report includes the specific modules, URLs, and behaviors above for investigators and defenders.
Malvertising Campaign Distributes Trojanized Microsoft Teams Installer to Deliver Oyster Backdoor
Source: Insikt Group | Validated Intelligence Event
IOC: Domain - nickbush24[.]com
IOC: SHA256 Hash - d46bd618ffe30edea56561462b50eb23feb4b253316e16008d99abb4b3d48a02
On 26 September 2025, cybersecurity firms Conscia and Blackpoint Cyber published aligned technical analyses of a malvertising campaign that used trojanised Microsoft Teams installers to deliver the Oyster backdoor. The actors used SEO poisoning and rogue advertisements to redirect users searching for genuine Microsoft Teams installers to malicious domains such as teams-install[.]icu and teams-install[.]top; one documented chain redirected from bing[.]com → team[.]frywow[.]com → teams-install[.]icu. At the time of the analysis those domains returned error messages. The fraudulent installers were signed with digital certificates issued to entities including KUTTANADAN CREATIONS INC., 4th State Oy and NRM NETWORK RISK MANAGEMENT INC.; those certificates remained valid for roughly two days, enabling the threat actors to bypass signature-based detection and narrow the window for certificate revocation.
According to Blackpoint Cyber, the trojanised installer (MSTeamsSetup.exe) drops a DLL named CaptureService.dll into the user’s AppData\Roaming folder, then creates a scheduled task (“Capture Service”) that invokes rundll32.exe to run the DLL every eleven minutes; CaptureService.dll installs the Oyster backdoor. Oyster was observed communicating with multiple command-and-control hosts, including nickbush24[.]com, techwisenetwork[.]com, maddeehot[.]online, server-na-qc2[.]farsafe[.]net and the IPs 45[.]66[.]248[.]112, 54[.]39[.]83[.]187 and 185[.]28[.]119[.]228; at the time of writing those C2 servers returned error messages.
Sandbox and static analysis flagged the sample as malicious: it enumerates processes, drops CaptureService.dll (SHA256: d46bd618ffe30edea56561462b50eb23feb4b253316e16008d99abb4b3d48a02) and executes it via rundll32.exe, creates and runs the scheduled task, sends DNS requests (for example to nickbush24[.]com), checks for mouse activity to detect sandboxes/VMs, gathers system information and default language, terminates processes, issues HTTP GET/POST requests to endpoints such as hxxps://cybersavvynetwork[.]com/api/kcehc and hxxps://nickbush24[.]com/reg (which returned errors at the time of analysis), creates the mutex “7GhJ-2KlM-8NpQ-7RsT-9UvW-0XyZ-LmNo-PqKs” to prevent reinfection, and detects debuggers using timing checks (GetTickCount) and IsDebuggerPresent.
Remediation Actions
Following the information provided above, we recommend that the technologies mentioned be fully patched and updated. We also want to highlight and recommend applying the following patches where applicable:
- CVE-2025-41250, CVE-2025-41251, CVE-2025-41252: These vulnerabilities can be remediated by updating vCenter and NSX to the most recent version.
- CVE-2025-20352: We recommend updating SNMP versions v1, v2c, v3 and IOS and IOS XE to the most recent version to prevent this vulnerability from being exploited.
- CVE-2025-56383: There has not yet been a patch released for this CVE, we advise updating this once an update becomes available.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing related searching and hunting activities within your environment.
