Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
DrayTek Patches CVE-2025-10547 Affecting Vigor Routers - On 2 October 2025, DrayTek released a patch for CVE-2025-10547, a vulnerability in its DrayOS-based Vigor routers caused by an uninitialised variable. The flaw could be exploited by an attacker with access to the local network through specially crafted HTTP or HTTPS requests sent to the router’s Web User Interface (WebUI). Such exploitation might lead to memory corruption, system crashes, denial-of-service (DoS) attacks, or even remote code execution (RCE). At present, there are no indications that the vulnerability has been exploited in the wild.
DrayTek has advised that the risk of WAN-based exploitation can be reduced by disabling remote WebUI and SSL VPN access or by using Access Control Lists (ACLs). The company’s security advisory details which router models are affected and provides recommended firmware updates for each. Organisations are urged to install the latest firmware updates promptly to minimise exposure to potential attacks.
Redis Patches Lua Use-After-Free Vulnerability (CVE-2025-49844) - On 3 October 2025, Redis released a security advisory for CVE-2025-49844, a critical remote code execution (RCE) vulnerability that affects all Redis versions supporting Lua scripting. The flaw, discovered by Wiz during Pwn2Own Berlin and dubbed “RediShell”, was first reported to Redis in May 2025. Wiz identified around 330,000 Redis instances exposed to the internet, including approximately 60,000 without authentication enabled. At present, there are no known cases of active exploitation of this vulnerability.
CVE-2025-49844 is a use-after-free (UAF) vulnerability within Redis’s Lua scripting engine, which allows attackers to manipulate the garbage collector. By exploiting this flaw with carefully crafted Lua scripts, a threat actor could break out of the interpreter sandbox and execute arbitrary code, potentially leading to complete system compromise. Redis has addressed the issue in multiple patched releases across both commercial and open-source editions, and users are strongly encouraged to update to the latest versions to mitigate the risk.
Cisco Talos Discloses Six Vulnerabilities Affecting NVIDIA CUDA Toolkit and Adobe Acrobat Reader - On 1 October 2025, Cisco Talos reported five vulnerabilities in the NVIDIA CUDA Toolkit and one in Adobe Acrobat Reader. Both NVIDIA and Adobe addressed these issues in September 2025. At the time of writing, there are no known reports of active exploitation in the wild.
The NVIDIA vulnerabilities include CVE-2025-23339, a stack-based buffer overflow in cuobjdump 12.8.55, and several issues in nvdisasm 12.8.90, including improper array index validation (CVE-2025-23338), out-of-bounds reads and writes (CVE-2025-23340 and CVE-2025-23271), and a heap-based buffer overflow (CVE-2025-23308). These flaws could allow attackers to execute arbitrary code, cause denial-of-service conditions, or corrupt memory via specially crafted ELF files. The Adobe vulnerability, CVE-2025-54257, is a use-after-free issue in Acrobat Reader’s page property functionality, which could be exploited by opening a malicious PDF, potentially leading to arbitrary code execution and memory corruption.
Potential Threats
China-Linked Threat Group UAT-8099 Conducts SEO Fraud and Credential Theft via Compromised Microsoft IIS Servers - On 2 October 2025, Cisco Talos reported that the Chinese‑speaking threat group “UAT‑8099” had compromised Microsoft IIS servers at universities, tech firms, and telecom providers in India, Thailand, Vietnam, Canada, and Brazil. The group exploited an unrestricted file‑upload vulnerability to install a web shell, enable hidden accounts, escalate privileges, and activate RDP for persistence. They extracted credentials using publicly available tools, stored them in hidden directories, and maintained connectivity via SoftEther VPN, EasyTier, and Fast Reverse Proxy (FRP). Talos linked the activity to a Chinese‑speaking actor based on linguistic and procedural indicators.
UAT‑8099 deployed multi-stage payloads via scheduled tasks and DLL sideloading to launch Cobalt Strike Beacon, using CDN-style URLs and Exchange-like ports to evade detection. They also installed BadIIS malware, which operated in proxy, injector, and SEO-fraud modes - fetching content from C2 servers, injecting malicious JavaScript into web pages, and serving backlink HTML to manipulate search rankings. A component called D_Safe_Manage was also installed to protect the compromise and prevent interference with the malware.
Threat Actors Use JuicyPotato and XiebroC2 to Target MS-SQL Servers - On September 29, 2025, AhnLab Security Intelligence Center (ASEC) reported a campaign targeting poorly secured MS-SQL servers using the open-source XiebroC2 command-and-control framework. Unlike earlier coin-mining campaigns, this operation demonstrated escalation by installing a privilege-escalation tool and remote-control framework. The threat actors gained access through brute-force or dictionary attacks against MS-SQL servers with weak credentials, then deployed the JuicyPotato tool to elevate privileges.
After privilege escalation, the attackers used PowerShell to download XiebroC2 from hxxp://183[.]196[.]14[.]213:2780/tee[.]exe (now inactive). Once executed, XiebroC2 collected system identifiers such as process ID, hardware ID, and username, then connected to a command-and-control server at 1[.]94[.]185[.]235 over port 8433 using a reverse WebSocket protocol to await commands. ASEC advised securing exposed MS-SQL servers, enforcing strong credentials, and monitoring for JuicyPotato or unusual outbound network activity.
ProSpy and ToSpy Android Spyware Campaigns Target UAE by Impersonating Signal and ToTok - On 2 October 2025, ESET reported two Android spyware campaigns targeting users in the UAE by impersonating Signal and ToTok. The campaigns use phishing sites and fake app stores to distribute malicious APKs, as neither spyware variant is available on official app stores.
The ProSpy campaign, active since 2024, spreads fake “Signal Encryption Plugin” or “ToTok Pro” apps, which request extensive permissions, hide to evade detection, and exfiltrate SMS, contacts, files, and device data. The ToSpy campaign, active since mid-2022, delivers trojanised ToTok apps via phishing sites, including a Samsung Galaxy Store mimic, and steals device data, files, and chat backups while maintaining persistence through foreground services, boot persistence, and scheduled restarts.
General News
Jaguar Land Rover to restart production following cyberattack - Jaguar Land Rover (JLR) announced a phased restart of its global manufacturing operations following a cyberattack last month that halted production entirely. To support affected suppliers, the company is launching a financing scheme providing upfront cash and accelerated payments, helping them overcome the financial strain caused by the shutdown. The disruption was described by one senior politician as “a cyber shockwave” threatening potentially thousands of jobs. JLR, which reported £2.5 billion in pre-tax profits and £29 billion in revenue this year, secured two loans - including one government-backed - to restart production for itself and its supply chain.
The government-backed loan drew some criticism, with questions raised over why JLR, owned by the wealthy Tata conglomerate, required state support. The cyberattack was framed as an economic security incident, highlighting the broader impact on Britain’s automotive sector, which accounts for around 4% of national goods exports. JLR CEO Adrian Mardell confirmed the restart of production at the Wolverhampton engine plant, followed by Nitra and Solihull car plants, and emphasised that suppliers were “central to our success,” with the new financing scheme designed to accelerate payments by up to 120 days. Mardell thanked staff and partners for their efforts and said recovery was “firmly underway.”
Discord says sensitive info stolen during cyberattack on customer service provider - On 3 October 2025, Discord warned users that a cyberattack on a third-party customer service provider exposed sensitive information of an unspecified number of customers. The breach, which occurred on 20 September, targeted users who had contacted Discord’s customer support or trust and safety teams. Stolen data includes names, usernames, emails, IP addresses, messages exchanged with support, and billing information such as the last four digits of credit cards and purchase histories. In a few cases, images of government IDs used for age verification appeals were also accessed. Training materials and internal presentations were additionally stolen.
Discord stated that hackers attempted to extort the company but never accessed its systems directly. The company revoked the third-party provider’s access, launched an internal investigation with a forensics firm, and involved law enforcement. Discord is contacting affected users, notifying relevant data protection authorities, and reviewing security controls for third-party support providers. The number of impacted users and the identity of the breached third party have not been disclosed.
Renault UK Discloses Third-Party Breach Exposing Customer Contact and Vehicle Data - On 2 October 2025, Renault UK reported a cyberattack on an undisclosed third-party data processing firm that may have exposed customer information, including names, gender, postal addresses, emails, phone numbers, vehicle registration numbers, and VINs. Renault confirmed that no financial account or password data was compromised.
The company stated the incident was isolated and contained, with internal systems unaffected, and has notified authorities while cooperating with the affected provider. Renault advised customers to ignore any password requests via email or phone. Insikt Group found no evidence of Renault UK data appearing on dark web or ransomware sites.
Threat Actor Weekly Graph
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group's severity. These updates can be seen below.
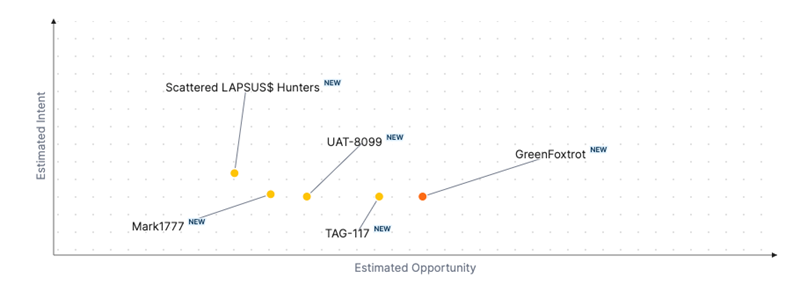
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Increase | Opportunity | Intent | ||||||
|---|---|---|---|---|---|---|---|---|---|
| GreenFoxtrot | NEW | → | ● Moderate | NEW | → | ● 51 | NEW | → | ● 25 |
| TAG-117 | NEW | → | ● Basic | NEW | → | ● 45 | NEW | → | ● 25 |
| Scattered LAPSUS$ Hunters | NEW | → | ● Basic | NEW | → | ● 25 | NEW | → | ● 35 |
|
UAT-8099 |
NEW | → | ● Basic | NEW | → | ● 35 | NEW | → | ● 25 |
| Mark1777 | NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 26 |
Global Trends Powered by Recorded Future
Within each category, we have provided the current top five globally trending items. Each item is linked to how actively trending it is and is marked with a small symbol.
The spikes in references are calculated over 60 days and are normalised to ensure they aren't disproportionate when compared to bigger entities that will naturally have more baseline mentions.
▲- Spike – This indicates a large increase in reporting volume and a high diversity in the event descriptions,
▲- Rise – This indicates a small increase in reporting volume with little diversity in the descriptions.
| Attackers | Methods | Vulnerabilities | Targets | ||||
|---|---|---|---|---|---|---|---|
| Crimson Collective | ▲ |
Credential Stuffing |
▲ | CVE-2025-61882 | ▲ |
PancakeSwap |
▲ |
|
RipperSec |
▲ |
Remote Code Execution |
▲ | CVE-2025-10035 | ▲ |
Willias & Connolly |
▲ |
|
Cyber Partisans |
▲ | Clop Ransomware | ▲ | CVE-2025-59489 | ▲ |
IBM |
▲ |
|
Scattered LAPSUS$ Hunters |
▲ |
PlugX (SOGU.SEC) |
▲ | CVE-2025-61984 | ▲ |
Red Hat |
▲ |
|
ShinyHunters |
▲ |
DDoS |
▲ |
CVE-2025-57819 |
▲ |
Interactive Entertainment |
▲ |
Prominent Information Security Events
China-Linked Threat Group UAT-8099 Conducts SEO Fraud and Credential Theft via Compromised Microsoft IIS Servers
Source: Insikt Group | Validated Intelligence Event
IOC: SHA256 Hash - cbb4a9172f4b0185d3aecbaa60b8e04d8910889da8905e5089df3efdec0a38dd
IOC: Domain - ar[.]mnnoxzmq[.]com
On 2 October 2025, Cisco Talos reported that a previously unknown Chinese-speaking threat group, tracked as “UAT-8099,” had compromised Microsoft IIS servers belonging to universities, technology companies, and telecommunications providers across India, Thailand, Vietnam, Canada, and Brazil. The group conducted credential theft and search engine optimisation (SEO) fraud using remote desktop protocol (RDP), Cobalt Strike Beacon, and BadIIS malware. Talos attributed the campaign to a Chinese-speaking actor based on linguistic artefacts and tactics, techniques, and procedures (TTPs) matching previous operations linked to similar threat actors.
The attack began with UAT-8099 exploiting an unrestricted file-upload vulnerability to install an ASP.NET web shell and run reconnaissance commands. The group enabled guest and hidden accounts, escalated privileges to administrator level, and activated RDP for persistent access. Using batch scripts, the attackers configured RDP and firewall settings, maintained out-of-band connectivity via SoftEther VPN, EasyTier, and Fast Reverse Proxy (FRP), and extracted credentials with publicly available tools like Procdump, compressing the stolen data into hidden directories. They also conducted extensive file system searches and inspected certificate files to gather additional sensitive information.
Talos observed the deployment of multi-stage payloads via a custom DLL (wmicodegen.dll) that launched a reflective loader deploying Cobalt Strike Beacon in memory, using CDN-style URLs and Exchange-like ports to blend with legitimate traffic. Concurrently, UAT-8099 installed an IIS module running the BadIIS malware, which operated in three modes: proxy, injector, and SEO fraud, allowing content fetching from secondary C2s, JavaScript injection into HTML pages, and manipulation of search engine rankings. The group also installed D_Safe_Manage to secure the compromised servers and prevent interference with BadIIS operations.
Threat Actors Use JuicyPotato and XiebroC2 to Target MS-SQL Servers
Source: Insikt Group | Validated Intelligence Event
IOC: IP - 1[.]94[.]185[.]235
IOC: SHA256 Hash - 0212bde3715a349a6b684dd54548638b5899be8d62a1e25559937e494e3cce54
On 29 September 2025, AhnLab Security Intelligence Center (ASEC) published a technical analysis of a campaign abusing improperly managed MS-SQL servers to deploy the XiebroC2 framework. XiebroC2 is an open-source, Go-based command-and-control framework that supports implants for Windows, Linux and macOS. Unlike prior MS-SQL campaigns that typically installed coin miners, ASEC observed this operation escalate capabilities by installing a privilege-escalation tool and a remote-control framework.
ASEC reported that actors gained initial access by conducting brute-force or dictionary attacks against externally exposed MS-SQL servers using weak or poorly managed credentials. After access was obtained they deployed JuicyPotato to exploit process tokens and elevate privileges, then used PowerShell to download XiebroC2 (noted as coming from hxxp://183[.]196[.]14[.]213:2780/tee[.]exe, which returned an error at the time of analysis).
Once executed, the XiebroC2 implant collected host artefacts — including PID, HWID, computer name and the logged-in username — and established a connection to a C2 server at 1[.]94[.]185[.]235 over port 8433 using a Session/Reverse_Ws protocol to await further instructions. Defenders should prioritise securing exposed MS-SQL services, enforce strong credential and access-control practices, and monitor for JuicyPotato usage and unusual outbound connections to the reported C2 infrastructure.
Remediation Actions
Following the information provided above, we recommend that the technologies mentioned be fully patched and updated. We also want to highlight and recommend applying the following patches where applicable:
- CVE-2025-10547: This DrayTek vulnerability can be remediated by updating to the most recent patch.
- CVE-2025-49844: Redis has released multiple patches across both commercial and open-source editions, and strongly encourage users to update to the most recent versions to mitigate this risk.
- CVE-2025-23339: Nvidia have patched this stack-based buffer overflow vulnerability, updating to the most recent patches from September 2025 will remediate this vulnerability.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing related searching and hunting activities within your environment.
