Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
Threat Actors Actively Exploit Wordfence Service Finder Bookings Flaw, CVE-2025-5947 - On October 7, 2025, Wordfence Intelligence reported active exploitation of CVE-2025-5947 affecting Service Finder Bookings plugin (versions ≤ 6.0), allowing threat actors to bypass authentication and impersonate any user, including administrators. No publicly confirmed number of organisations has been disclosed; however, Wordfence has blocked over 13,800 exploit attempts.
CVE-2025-5947 allows unauthenticated account takeover and privilege escalation due to improper validation of the original_user_id cookie in the service_finder_switch_back() function. This flaw enables threat actors to trigger the wp_set_auth_cookie() function through a crafted HTTP GET request, leading to complete site compromise. Aonetheme patched CVE-2025-5947 in version 6.1 on July 17, 2025. However, many sites may remain unpatched.
Technical Blog and Alleged PoC for Control Character Injection Vulnerability in OpenSSH ProxyCommand (CVE-2025-61984) - OpenSSH control-character injection allows command execution. Researcher David Leadbeater published a technical write-up (Oct 7, 2025) describing CVE-2025-61984: a control-character injection flaw in OpenSSH’s ProxyCommand handling that lets attackers embed control characters (eg. newline \n) in usernames to break shell parsing and execute subsequent commands. OpenSSH 10.1 (released Oct 6, 2025) fixes the bug by rejecting control characters in valid_ruser (using iscntrl()).
The issue arises when ProxyCommand expands the %r token into a shell command and the username contains control characters: shells like Bash, Fish and csh can continue execution after a syntax error, allowing an injected newline to run attacker-controlled commands.
CVE-2025-20362, an Actively Exploited Missing Authorisation Vulnerability in Cisco ASA and FTD - Cisco ASA/FTD WebVPN auth bypass and overflow exploited in the wild, Rapid7 (Oct 6, 2025) disclosed CVE-2025-20362, a path-traversal that allows unauthenticated access to the WebVPN file upload handler; CISA added CVE-2025-20362 (and linked CVE-2025-20333) to its KEV on Sept 25, 2025 and Insikt Group reported threat actors chaining the two (Sept 26) to deploy RayInitiator and LINE VIPER.
The issue arises when a //.. traversal reaches file_action.html and, when paired with the Lua upload handler bug, an oversized multipart boundary can overflow an 8,192-byte buffer (crash/reboot and potential further exploitation).
Potential Threats
Cl0p Exploited CVE-2025-61882, an Oracle E-Business Suite Zero-Day Vulnerability, for Data Theft - An Oracle EBS zero-day has been exploited by CL0P. Insikt/GTIG/Mandiant reporting and Oracle’s emergency advisory confirm CVE-2025-61882 is a critical, unauthenticated RCE in Oracle E-Business Suite that has been actively exploited since mid-2025 in extortion/data-theft operations attributed to CL0P-linked actors. Evidence shows multiple exploit chains were used to create malicious XSL/DB templates that execute Java payloads in memory, and that attackers later performed post-compromise reconnaissance and data exfiltration.
Campaign activity included targeted executive extortion emails and use of compromised third-party mailboxes to increase credibility; public reporting and telemetry point to scanning/probing and C2 infrastructure tied to the campaign.
Loader Dropped by Trojanized Termius App to Deliver ZuRu macOS Backdoor - On 11 July 2025, Insikt Group published a TTP instance on a campaign reported by SentinelOne in which threat actors deployed a new ZuRu variant via a trojanised Termius application bundle. ZuRu is a persistent macOS backdoor first observed in 2021 and previously distributed through poisoned Baidu search results. It resurfaced in May 2025 embedded within a trojanised copy of Termius, a legitimate secure-shell (SSH) management application.
The trojanised Termius app embeds two unauthorised binaries into the Termius Helper application: “.Termius Helper1”, a modified helper binary, and “.localized”, a Mach-O loader. This loader marks a tradecraft shift for ZuRu by replacing the prior dylib-based loading technique with an embedded helper binary strategy. The loader stages, executes and updates a secondary payload: a modified Khepri command-and-control beacon.
Threat Actor TA585 Delivers Stealer Malware via ClickFix and GitHub-Themed Phishing Campaigns - Between April and August 2025, threat actor TA585 ran phishing campaigns using ClickFix and GitHub-themed lures to deliver stealer malware such as LummaC2, Rhadamanthys, and MonsterV2, according to Proofpoint’s 13 October report. The group managed its operations through an infrastructure cluster dubbed “CoreSecThree,” which handled filtering, delivery, and malware deployment without relying on external brokers.
TA585’s ClickFix campaign redirected victims via injected JavaScript on legitimate sites, displaying fake CAPTCHA overlays that prompted users to run a PowerShell command downloading SonicCrypt-packed MonsterV2 and Rhadamanthys. The GitHub-themed operation exploited legitimate notification emails from fake issues in actor-controlled repositories, leading to similar PowerShell execution and payload delivery. Across both campaigns, infections enabled credential theft, data exfiltration, and remote access on compromised systems.
General News
UK hit by record surge in major cyberattacks - The National Cyber Security Centre (NCSC) will announce a record number of “nationally significant” cyber incidents in its 2024 Annual Review, revealing that staff responded to 429 attacks between September 2024 and August 2025. Of these, 204 were classed as nationally significant, more than double the 89 recorded the previous year. 18 attacks were deemed “highly significant,” the second-most severe category, affecting central government, critical services, or major economic sectors.
The spike follows a wave of disruptive attacks on UK industries, including the month-long outage at Jaguar Land Rover (JLR), which experts described as “an economic security incident” rather than a mere corporate disruption. In response, the government is writing to FTSE 350 CEOs and chairs urging “concrete action” to bolster defences amid what officials call a surge in “intense, frequent, and sophisticated” cyber threats targeting British enterprises.
Ukraine moves closer to forming dedicated military Cyber Force - Ukraine’s parliament has advanced plans to establish a new Cyber Force within the Armed Forces, approving a bill in its first reading that would unite the country’s offensive and defensive cyber capabilities under a single command. If passed in a second vote and signed by President Volodymyr Zelensky, the Cyber Force would conduct military cyber operations, gather intelligence, defend critical systems, and align Ukraine’s capabilities more closely with NATO standards as it seeks full membership.
The new branch would initially receive a 14 million hryvnia ($336,000) budget in 2025 to build its infrastructure. A key feature of the proposal is the creation of a cyber reserve, a pool of civilian tech experts who can be mobilized to support military operations without enlisting full-time. Cybersecurity leaders have welcomed the initiative, saying it would strengthen collaboration between Ukraine’s military and its world-renowned tech sector, which has played an active role in digital defence since Russia’s invasion.
4chan fined by UK regulator under Online Safety Act - Ofcom has fined imageboard 4chan £20,000 ($26,000) for failing to comply with the UK’s Online Safety Act, marking the first financial penalty issued to a major online platform under the new law. The fine will rise by £100 ($133) per day from Tuesday until compliance is achieved. While modest in value, the move signals an escalating regulatory stance that could ultimately see British internet service providers ordered to block access to 4chan entirely.
The Online Safety Act requires platforms hosting user-generated content to safeguard users from harmful or illegal material. Ofcom has already warned adult content sites that failure to verify users’ ages by July could result in fines of up to £18 million or 10% of global turnover, alongside potential domain blocks.
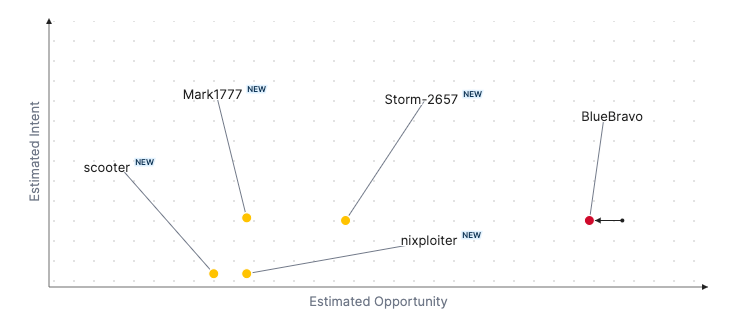
Threat Actor Weekly Graph
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group's severity. These updates can be seen below.
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Increase | Opportunity | Intent | ||||||
|---|---|---|---|---|---|---|---|---|---|
| BlueBravo | ● High | → | ● High | ● 87 | → | ● 82 | ● 25 | → | ● 25 |
| Storm-2657 | NEW | → | ● Basic | NEW | → | ● 45 | NEW | → | ● 25 |
| Mark1777 | NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 26 |
|
Nixploiter |
NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 5 |
| Scooter | NEW | → | ● Basic | NEW | → | ● 25 | NEW | → | ● 5 |
Global Trends Powered by Recorded Future
Within each category, we have provided the current top five globally trending items. Each item is linked to how actively trending it is and is marked with a small symbol.
The spikes in references are calculated over 60 days and are normalised to ensure they aren't disproportionate when compared to bigger entities that will naturally have more baseline mentions.
▲- Spike – This indicates a large increase in reporting volume and a high diversity in the event descriptions,
▲- Rise – This indicates a small increase in reporting volume with little diversity in the descriptions.
ByteToBreach
| Attackers | Methods | Vulnerabilities | Targets | ||||
|---|---|---|---|---|---|---|---|
| Black Ember | ▲ |
TA0043 (Reconnaissance) |
▲ | CVE-2025-61984 | ▲ |
GoogleCloudPlatform |
▲ |
|
Exsploit Wmc |
▲ |
AlphaLocker |
▲ | CVE-2018-7600 | ▲ |
Oracle |
▲ |
|
Anonymous |
▲ | LummaC2 | ▲ | CVE-2025-11577 | ▲ |
IBM |
▲ |
| ByteToBreach | ▲ |
Monti Ransomware |
▲ | CVE-2025-4008 | ▲ |
Red Hat |
▲ |
|
BlackNevas Ransomware Group |
▲ |
ClayRat |
▲ |
CVE-2025-1829 |
▲ |
Sonicwall VPN |
▲ |
Prominent Information Security Events
Threat Actor TA585 Delivers Stealer Malware via ClickFix and GitHub-Themed Phishing Campaigns
Source: Insikt Group | Validated Intelligence Event
IOC: SHA256 Hash - 666944b19c707afaa05453909d395f979a267b28ff43d90d143cd36f6b74b53e
IOC: Domain - analyticanodec[.]com
IOC: IP - 91.200.14.69
On 2 October 2025, Cisco Talos reported that a previously unknown Chinese-speaking threat group, tracked as “UAT-8099,” had compromised Microsoft IIS servers belonging to universities, technology companies, and telecommunications providers across India, Thailand, Vietnam, Canada, and Brazil. The group conducted credential theft and search engine optimisation (SEO) fraud using remote desktop protocol (RDP), Cobalt Strike Beacon, and BadIIS malware. Talos attributed the campaign to a Chinese-speaking actor based on linguistic artefacts and tactics, techniques, and procedures (TTPs) matching previous operations linked to similar threat actors.
The attack began with UAT-8099 exploiting an unrestricted file-upload vulnerability to install an ASP.NET web shell and run reconnaissance commands. The group enabled guest and hidden accounts, escalated privileges to administrator level, and activated RDP for persistent access. Using batch scripts, the attackers configured RDP and firewall settings, maintained out-of-band connectivity via SoftEther VPN, EasyTier, and Fast Reverse Proxy (FRP), and extracted credentials with publicly available tools like Procdump, compressing the stolen data into hidden directories. They also conducted extensive file system searches and inspected certificate files to gather additional sensitive information.
Talos observed the deployment of multi-stage payloads via a custom DLL (wmicodegen.dll) that launched a reflective loader deploying Cobalt Strike Beacon in memory, using CDN-style URLs and Exchange-like ports to blend with legitimate traffic. Concurrently, UAT-8099 installed an IIS module running the BadIIS malware, which operated in three modes: proxy, injector, and SEO fraud, allowing content fetching from secondary C2s, JavaScript injection into HTML pages, and manipulation of search engine rankings. The group also installed D_Safe_Manage to secure the compromised servers and prevent interference with BadIIS operations.
Loader Dropped by Trojanized Termius App to Deliver ZuRu macOS Backdoor
Source: Insikt Group | Validated Intelligence Event
IOC: URL - hxxp[:]//download[.]termius[.]info/bn[.]log[.]md5
IOC: SHA256 Hash - 42605f1d22f8d38f0be494f36d377bf71592ae54583e6e78641a63ec3021cbeb
On 11 July 2025, Insikt Group published a TTP instance expanding on a campaign reported by SentinelOne in which threat actors deployed a new ZuRu variant via a trojanised Termius application bundle. ZuRu is a persistent macOS backdoor first observed in 2021 and previously distributed via poisoned Baidu search results; it resurfaced in May 2025 packaged inside a trojanised copy of Termius, a legitimate SSH management application.
The malicious Termius bundle embeds two unauthorised binaries into the Termius Helper: “.Termius Helper1”, a modified helper binary, and “.localized”, a Mach-O loader. This note focuses on the internal behaviour of the loader (SHA256: 42605f1d22f8d38f0be494f36d377bf71592ae54583e6e78641a63ec3021cbeb), detailing its persistence, single-instance guarantees, update mechanism, and reuse of legacy artefacts to illustrate how the malware maintains execution and complicates analysis. Notably, the loader marks a tradecraft shift for ZuRu by moving away from a dylib-based loader toward an embedded helper binary strategy that stages, executes and updates a secondary payload: a modified Khepri command-and-control beacon.
On execution, .localized performs a relocation check via a function named _copySelfToShare(): if the binary is not already under /Users/Shared/ it copies itself there as com.apple.xssooxxagent, overwriting any existing file. It then drops a LaunchDaemon plist to /Library/LaunchDaemons/com.apple.xssooxxagent.plist to schedule hourly execution and uses a helper routine, _writePlistAndStartDaemon(), to refresh the daemon lifecycle by issuing launchctl bootout and bootstrap commands. These operations require elevated privileges; the loader reintroduces the deprecated AuthorizationExecuteWithPrivileges API used by earlier ZuRu variants to request those rights.
Remediation Actions
Following the information provided above, we recommend that the technologies mentioned be fully patched and updated. We also want to highlight and recommend applying the following patches where applicable:
- CVE-2025-5947: Updating the associated Wordpress plugin to the latest available version will help mitigate this risk.
- CVE-2025-61984: Updating to the newly released OpenSSH 10.1, which rejects control characters in usernames can mitigate this vulnerability.
- CVE-2025-20362: Applying Cisco's recommended vendor patches, added to KEV in September 2025 can help mitigate this risk.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing related searching and hunting activities within your environment.
