Executive Summary -
Highlights of Cyber Threat Intelligence Digest
Vulnerabilities
Dell Patches Three Vulnerabilities (CVE-2025-43995, CVE-2025-43994, CVE-2025-46425) in Dell Storage Manager - On 24 October 2025, Dell released patches for three vulnerabilities affecting Dell Storage Manager. These issues were addressed in version 2020 R1.22, and at the time of writing, there have been no reports of these vulnerabilities being exploited in the wild. The patches aim to mitigate risks associated with improper authentication, missing authentication, and improper restriction of XML external entity references within the software.
The specific vulnerabilities include CVE-2025-43995, a critical-severity improper authentication flaw that could allow threat actors to bypass protection mechanisms in the DSM Data Collector using a specially crafted SessionKey and UserId. CVE-2025-43994 is a high-severity missing authentication vulnerability for a critical function that could enable disclosure of sensitive information. CVE-2025-46425 is a medium-severity vulnerability involving improper restriction of XML external entity references, which could allow unauthorised access to compromised devices. All of these affect Dell Storage Manager versions DSM 20.1.21.
Apache Patched Three Vulnerabilities (CVE-2025-55752, CVE-2025-55754, and CVE-2025-61795) in Apache Tomcat - On 28 October 2025, Apache released patches for three vulnerabilities affecting Apache Tomcat, identified as CVE-2025-55752, CVE-2025-55754, and CVE-2025-61795. These vulnerabilities were addressed in versions 11.0.12, 10.1.47, and 9.0.110. At the time of writing, there have been no reports of these issues being exploited in the wild. The updates aim to address critical security weaknesses that could impact access control, resource management, and server stability.
The specific vulnerabilities include CVE-2025-55752, a path traversal flaw that could allow threat actors to bypass access controls and upload malicious files via HTTP PUT requests, potentially leading to remote code execution. CVE-2025-55754 is a console manipulation vulnerability that could permit injection of ANSI escape sequences through a specially crafted URL. CVE-2025-61795 involves improper resource shutdown or release, which could enable attackers to trigger denial-of-service conditions. These vulnerabilities affect multiple versions of Apache Tomcat, ranging from early 9.0, 10.1, and 11.0 releases up to the patched versions.
Microsoft Addresses Critical ASP.NET Core Vulnerability CVE-2025-55315 - On 22 October 2025, Microsoft updated its advisory for a critical vulnerability affecting ASP.NET Core, identified as CVE-2025-55315. Organisations running .NET 8 or later are advised to apply the latest updates, while those using .NET 2.3 should update the ‘Microsoft.AspNet.Server.Kestrel.Core’ package to version 2.3.6 and redeploy their applications. At the time of writing, there have been no reports of this vulnerability being exploited in the wild.
CVE-2025-55315 is a security feature bypass vulnerability caused by inconsistent HTTP request parsing between front-end and back-end servers. An authenticated threat actor with limited privileges could exploit this flaw to inject hidden HTTP requests that bypass authentication or request validation. Successful exploitation could allow user impersonation, unauthorised access to sensitive data, modification of files, or disruption of services, making it a serious risk for affected systems.
Potential Threats
Threat Group CryptoChameleon Targets LastPass Customers in Phishing Campaign - On 23 October 2025, LastPass disclosed that the threat group CryptoChameleon had launched a phishing campaign targeting its customers beginning in mid-October, with the aim of stealing credentials and cryptocurrency assets. LastPass attributed the campaign to CryptoChameleon based on domain overlaps, shared hosting infrastructure, and social engineering techniques consistent with the group’s previous operations. The group had previously used LastPass branding in a phishing kit observed in April 2024.
The mid-October campaign involved phishing emails claiming that a family member had submitted a death certificate to initiate a legacy vault access request. The emails contained fabricated case details and a malicious link prompting users to cancel the request, which redirected them to a spoofed LastPass domain designed to capture master passwords. Additional phishing infrastructure included domains impersonating Gmail and cryptocurrency platforms, as well as variants intended to compromise passkeys and other authentication mechanisms. CryptoChameleon also followed up with phone calls posing as LastPass representatives to pressure users into providing their credentials.
Threat Actors Deliver Baohuo Android Backdoor via Trojanized Telegram X Application to Hijack Telegram Accounts - On 23 October 2025, Doctor Web analysed Baohuo (Android.Backdoor.Baohuo.1.origin), an Android backdoor embedded in trojanised versions of Telegram X, targeting users in Brazil and Indonesia since mid‑2024. Baohuo can steal usernames, passwords, chat histories and clipboard content, and grants full control over compromised Telegram accounts, including joining or leaving chats, modifying channels and hiding sessions. Infections were reported on over 58,000 devices, including smartphones, tablets, Android TV boxes and in‑vehicle systems. Notably, it uses Redis databases for command‑and‑control, the first known case for Android malware.
Baohuo is distributed via malicious ads redirecting users to fake app stores and third‑party repositories hosting trojanised APKs. Once installed, it embeds into the Telegram X executable via DEX modification, LSPatch or dynamic loading, with execution triggered by the ApplicationLoader class. Using the Xposed framework, it conceals unauthorised devices, hides chats and shows phishing overlays. The malware updates its configuration from C2 servers over HTTP or HTTPS, retrieving Redis and NPS server details, though some of this infrastructure was unresponsive at the time of reporting.
YouTube Ghost Network Delivers Infostealers via Gaming Cheats and Cracked Software Lures - On 23 October 2025, Check Point reported that unidentified threat actors operated a “YouTube Ghost Network” that compromised YouTube accounts to distribute malware, including Rhadamanthys, Lumma Stealer, StealC, RedLine, 0debug and Phemedrone infostealers. Active since at least 2021, the network published over 3,000 malicious videos targeting users seeking game cheats and cracked software, with activity tripling in 2025. Compromised channels were used to post deceptive videos promoting cryptocurrency tools, gaming content and cracked Adobe software; descriptions and community posts contained links that redirected viewers to phishing pages hosting password‑protected archives with malicious installers, and victims were sometimes instructed to disable Windows Defender.
Check Point observed multiple delivery chains: in one campaign the installer executed the Rhadamanthys infostealer, which connected to a C2 server at 94[.]74[.]164[.]157:8888 to exfiltrate credentials and user data; in another the installer launched HijackLoader before deploying Rhadamanthys, which communicated with C2 servers such as 5[.]252[.]155[.]99. The threat actors regularly rotated payloads, archives and C2 infrastructure to maintain persistence, evade detection and sustain distribution across the platform.
General News
Russian-Linked Lynx Ransomware Allegedly Exfiltrates Sensitive Data From UK’s Dodd Group, Affecting Eight Military Sites - A Russian‑linked threat actor reportedly breached UK Ministry of Defence contractor Dodd Group on 23 September 2025, exfiltrating around 4TB of sensitive data tied to eight RAF and Royal Navy sites. The leaked material, released in stages under the name “Lynx Ransomware,” included project files, personnel lists, blueprints, site maps, base access applications, fleet and fuel records, and other operational documents. Initial assessments suggest the breach likely involved a supply‑chain compromise, with phishing or a malicious device also possible entry points.
Lynx Ransomware operates as a Russia‑linked RaaS group recruiting on underground forums while avoiding CIS targets. The Dodd Group breach reflects a broader trend of targeting contractors to access defence intelligence without directly attacking government networks. Such intrusions can disguise espionage as ransomware, giving actors schematics, access data and maintenance records that support operational targeting and intelligence collection.
Google disputes false claims of massive Gmail data breach - Google recently clarified that it had not suffered a data breach after numerous news outlets falsely reported that 183 million Gmail accounts were exposed. The confusion arose from a large compilation of credentials collected over the years via information-stealing malware, phishing, and other attacks, which were added to the Have I Been Pwned (HIBP) platform. These credentials were not obtained in a single breach, and the accounts affected span thousands of sites, not just Gmail. Google emphasised that its security remains strong and users are protected, noting that the reports were a misinterpretation of long-standing credential collections.
According to HIBP creator Troy Hunt, 91% of the 183 million credentials had previously been seen, with only 16.4 million being newly observed in any data breach. Collections like these are routinely used by companies, including Google, to warn users and enforce password resets when exposed credentials are detected. While the Gmail breach claims are false, exposed credentials remain a serious risk, as they can be leveraged by threat actors to access corporate networks or launch attacks. Google highlighted that sensationalised stories of unfounded breaches create unnecessary stress for users and business customers, following a similar incident last month where reports exaggerated a smaller breach affecting Google Workspace accounts.
New Android malware mimics human typing to evade detection, steal money - Researchers have identified Herodotus, a new Android banking trojan that mimics human behaviour to evade detection. Attributed to a developer known as K1R0 and analysed by ThreatFabric, the malware has been observed in campaigns in Italy and Brazil where it posed as apps such as Banca Sicura and Modulo Segurança Stone. It can display fake overlay pages over legitimate banking and crypto apps across multiple countries and is being advertised for sale on underground forums.
Herodotus spreads via SMS lures that prompt users to install a malicious APK. Once present, it waits for target apps, shows phishing overlays, intercepts SMS one‑time passcodes and abuses Android accessibility features. Unusually, remote control actions are “humanised”: the malware types characters individually with random pauses to resemble real typing, making automated‑behaviour detectors less effective. ThreatFabric warns banks and payment providers should pair behavioural analytics with device‑level checks to detect this evolving threat.
Threat Actor Weekly Graph
Over the past 7 days, we have been tracking the following intent and opportunity changes within our Threat Actor Landscape.
Intent represents the potential targets of a group. When a group is observed attacking a different organisation or entity, their intent will increase.
Opportunity represents the various methods and technologies these groups may use. For example, if a group started using a new attack vector, such as a new kind of ransomware, their opportunity would increase.
Both intent and opportunity are scored out of 100 and are responsible for scoring the group's severity. These updates can be seen below.
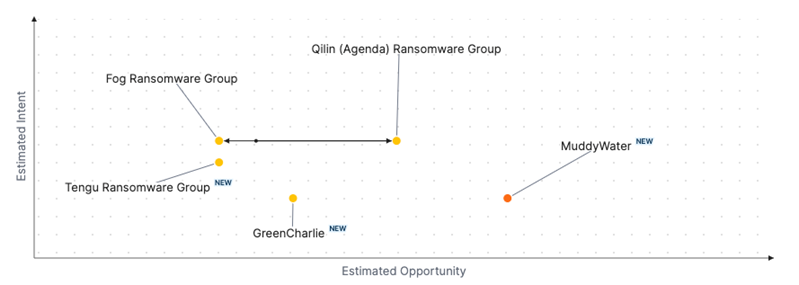
| ● Limited Severity | ● Basic Severity | ● Moderate Severity | ● High Severity |
| Threat Actor | Severity Increase | Opportunity | Intent | ||||||
|---|---|---|---|---|---|---|---|---|---|
| MuddyWater | NEW | → | ● Moderate | NEW | → | ● 64 | NEW | → | ● 25 |
| Tengu Ransomware Group | NEW | → | ● Basic | NEW | → | ● 25 | NEW | → | ● 40 |
| GreenCharlie | NEW | → | ● Basic | NEW | → | ● 35 | NEW | → | ● 25 |
|
Fos Ransomware Group |
● Basic | → | ● Basic | ● 49 | → | ● 25 | ● 49 | → | ● 49 |
| Qilin (Agenda) Ransomware Group | ● Basic | → | ● Basic | ● 30 | → | ● 49 | ● 49 | → | ● 49 |
Global Trends Powered by Recorded Future
Within each category, we have provided the current top five globally trending items. Each item is linked to how actively trending it is and is marked with a small symbol.
The spikes in references are calculated over 60 days and are normalised to ensure they aren't disproportionate when compared to bigger entities that will naturally have more baseline mentions.
▲- Spike – This indicates a large increase in reporting volume and a high diversity in the event descriptions,
▲- Rise – This indicates a small increase in reporting volume with little diversity in the descriptions.
| Attackers | Methods | Vulnerabilities | Targets | ||||
|---|---|---|---|---|---|---|---|
| Lazarus Group | ▲ |
Stealware |
▲ | CVE-2025-59287 | ▲ |
Power Utility |
▲ |
|
Safepay Ransomware Group |
▲ |
Account Takeover |
▲ | CVE-2025-2783 | ▲ |
Unified School District |
▲ |
|
Black Ember |
▲ | Clop Ransomware | ▲ | CVE-2025-54236 | ▲ |
Google Mail |
▲ |
| Central Intelligence Agency | ▲ |
Medusa Ransomware |
▲ | CVE-2025-40778 | ▲ | Global Data | ▲ |
|
Beregini |
▲ |
Data from Local System |
▲ |
CVE-2025-8088 |
▲ |
Verizon |
▲ |
Prominent Information Security Events
Threat Actors Deliver Baohuo Android Backdoor via Trojanized Telegram X Application to Hijack Telegram Accounts
Source: Insikt Group | Validated Intelligence Event
IOC: IP - 159[.]138[.]237[.]10
IOC: Domain - sdk-nps[.]ips5[.]info
On 23 October 2025, Doctor Web published an analysis of Baohuo (Android.Backdoor.Baohuo.1.origin), a backdoor found in trojanised Telegram X builds targeting users in Brazil and Indonesia since mid‑2024. Doctor Web says Baohuo can exfiltrate usernames, passwords, chat histories and clipboard contents, and can give operators full control of compromised Telegram accounts — joining or leaving chats, modifying channels and hiding authorised sessions. The researchers reported infections on more than 58,000 devices, including phones, tablets, Android TV boxes and in‑vehicle systems, and noted the campaign’s unique use of Redis for command‑and‑control.
The report describes delivery via malicious adverts that redirect victims to fake app‑store pages and third‑party repositories hosting trojanised APKs. After installation, Baohuo embeds into Telegram X by modifying the main DEX, applying an LSPatch, or dynamically loading a separate DEX; execution is initiated through an ApplicationLoader class so the backdoor runs in the foreground and blends with normal app behaviour. It also uses the Xposed framework to hook Telegram functions, concealing unauthorised devices, hiding chats and showing convincing phishing overlays.
Operationally, Baohuo fetches configuration from C2 servers over HTTP/HTTPS, obtaining Redis channels and NPS proxy details. It uploads SMS messages, contacts, clipboard contents and device metadata, collects lists of installed apps and message histories, polls for commands every minute and sends heartbeats every three minutes. The Redis pub/sub channel allows granular actions such as managing hidden‑chat blocklists, toggling authorised devices, prompting fake updates that redirect users, extracting Telegram databases via SQL queries and requesting authentication tokens, giving operators persistent control over compromised accounts and devices.
YouTube Ghost Network Delivers Infostealers via Gaming Cheats and Cracked Software Lures
Source: Insikt Group | Validated Intelligence Event
IOC: URL - hxxxs://5[.]252.155[.]231/gateway/3jw9q65j.b3tit
IOC: SHA256 Hash - b429a3e21a3ee5ac7be86739985009647f570548b4f04d4256139bc280a6c68f
On 23 October 2025, Check Point reported that unidentified threat actors were operating malware distribution campaigns through the "YouTube Ghost Network," compromising YouTube accounts to deliver infostealers including Rhadamanthys, Lumma Stealer, StealC, RedLine, 0debug and Phemedrone. Active since at least 2021, the network has published over 3,000 malicious videos targeting users seeking game cheats and cracked software, with activity tripling in 2025.
The actors reportedly compromised channels such as [@]Sound_Writer and [@]Afonesio1 to post deceptive videos promoting cryptocurrency tools, gaming content and cracked Adobe software. Links in video descriptions and community posts redirected viewers to phishing pages on Google Sites or Dropbox, hosting password-protected archives containing malicious installers. Victims were also instructed to disable Windows Defender to allow the malware to execute unhindered.
Check Point observed multiple delivery methods: in one campaign, the installer executed Rhadamanthys directly, connecting to a C2 server at 94[.]74[.]164[.]157:8888 to exfiltrate credentials; in another, the installer launched HijackLoader before deploying Rhadamanthys, which communicated with C2 servers such as 5[.]252[.]155[.]99. The threat actors rotated payloads, archives and C2 infrastructure to maintain persistence, evade detection and sustain distribution across the platform.
Remediation Actions
Following the information provided above, we recommend that the technologies mentioned be fully patched and updated. We also want to highlight and recommend applying the following patches where applicable:
- CVE-2025-43995, CVE-2025-43994, CVE-2025-46425: These vulnerabilities can be remediated by updating to version 2020 R1.22.
- CVE-2025-55752, CVE-2025-55754, CVE-2025-61795: These vulnerabilities have been addressed in versions 11.0.12, 10.1.47 and 9.0.110.
- CVE-2025-55315: Organisations running .NET 8 or later should apply the latest updates to remediate this vulnerability.
If you are currently an Acumen Cyber Vulnerability Management customer, we will be proactively performing related searching and hunting activities within your environment.
